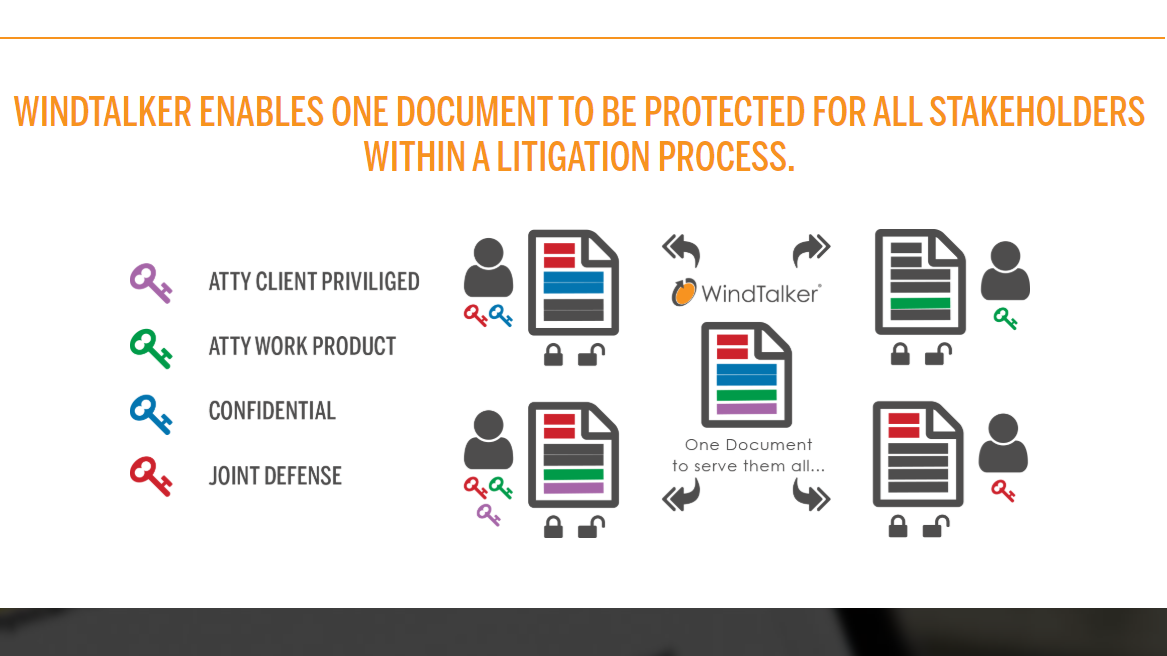
Two months ago, I reported on a preview I’d seen of WindTalker, describing it as a document-security product unlike anything I’d seen. This week, WindTalker makes its formal debut, launching as a cloud-based content-security platform with an initial focus on the legal sector.
Initially developed for the U.S. Department of Defense, WindTalker is…
 Robert Ambrogi Blog
Robert Ambrogi Blog